Signing up for Google Cloud Platform
The first step to preparing data storage on GCP is to create a account on GCP.Create a bucket within a project
Once you have your GCP account and a project within your account, a bucket and upload your data within the bucket either through the UI or CLI. You can leave all the settings during creation as the default. After creating your bucket, upload your data into the bucket.Create a Service Account
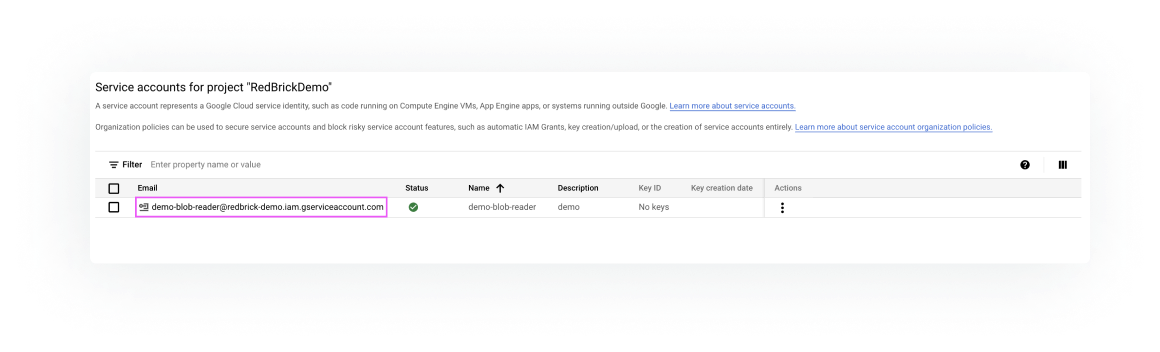
A service account is a special kind of account used by an application or a virtual machine (VM) instance, not a person. Applications use service accounts to make authorized API calls, authorized as either the service account itself, or as Google Workspace or Cloud Identity users through domain-wide delegation.- In the Cloud Console, go to the Service Accounts page.
- Select the appropriate project.
- Click Create service account.
-
Enter a service account name to display in the Cloud Console.
For eg,
gcs-blob-readerThe Cloud Console generates a service account ID based on this name. Edit the ID if necessary. You cannot change the ID later. - Optional: Enter a description of the service account.
- Click Create and continue to the next step.
-
Add the following two IAM roles to grant to the service account on the project.
- Storage Object Viewer (For reading the blobs from the GCS bucket)
- Service Account Token Creator (For pre-signing the blobs)
- If your bucket will be used as an annotation storage bucket, you need to give RedBrick AI access to PUT files as well.
- Once done adding roles, click Continue.
- Click Done to finish creating the service account.
- Note down the email id of the newly created service account.
Steps to give Bucket access to Service Account
- In the Cloud Console, go to the Bucket Browser page.
- Click on the more actions button (three dots) at the right of the necessary bucket.
-
Click on
Edit Bucket Permission. -
Click on
ADD PRINCIPAL. - Add the email address of the service account created in the above step (step 10).
- Add following two roles Storage Legacy Bucket Reader Storage Legacy Object Reader
- Click on save.\
Steps to create Service Account Key (JSON)
To use a service account from outside of Google Cloud, such as on other platforms or on-premises, you must first establish the identity of the service account. Public/private key pairs provide a secure way of accomplishing this goal. When you create a service account key, the public portion is stored on Google Cloud, while the private portion is available only to you.- In the Cloud Console, go to the Service Accounts page.
- Click the email address of the service account that we created in the above step.
- Click the Keys tab.
- Click the Add key drop-down menu, then select Create new key.
- Select JSON as the Key type and click Create.
- Clicking Create downloads a service account key file. After you download the key file, you cannot download it again.
Enable the Identity and Access Management (IAM) API
- In the Cloud Console, go to the API Library page.
- Select the appropriate project.
- Search for Identity and Access Management (IAM) API and click on it.
- Click on
Enable
Use this downloaded service account JSON key to create
GCS store in the Redbrick app.Configuring CORS
The final step in preparing your GCS bucket for use with RedBrick AI is enabling CORS on the bucket. Cross-Origin Resource Sharing allows the RedBrick AI application (with the domain https://app.redbrickai.com/) to make requests to your bucket. Please visit the following Google Cloud documentation for enabling CORS on a bucket - https://cloud.google.com/storage/docs/configuring-cors. You will want to use the following CORS JSON configuration file:If you’re also storing your annotations in your GCS bucket, be sure to add “PUT” to your method configuration array (e.g. “
["GET", "PUT"]”).Items Path
Once you’ve created your Google Storage method on RedBrick AI, you have to upload an Items List to your projects to import specific datapoints. Please have a look at the Items List documentation for an overview of the format for the JSON file. For data stored in an GCS bucket, theitems path needs to be formatted as follows:
root-folder is inside the GCS bucket storage method.